Building on our previous blog post on the importance and benefits of an ISMS, we delve deeper into the practical aspects of its implementation and its challenges. Whether you are an IT professional, a cyber security expert, or in a management role, this post will provide you with valuable insights into the best practices for a successful ISMS implementation and how to navigate common challenges.

Start your ISMS journey with these steps
The first key step for successful Information Security Management System (ISMS) implementation is to establish a strong project mandate. This includes defining the scope of the ISMS, setting clear objectives, and securing senior management commitment. The project mandate acts as a road map, guiding the organization throughout the implementation process. Read more about the most important steps in the following paragraphs.

1. Create an overview of your security posture
Generally, it is important to get a basic understanding of your current security posture. This could for example include the choice of the framework that you would like to work with and a basic evaluation of the current implementation of the controls. Check the requirements and evaluate in a very brief matter "am I already doing something for this topic or have I not touched this at all yet?". Like this, you can get a good understanding of how much you actually still need to do in order to get forward with the implementation of your ISMS.
Once you have identified what you have already covered with your current work, it will be easier to also identify potential risks. Please note, this does not nesseccarily need to be done as one of the first steps right away. There are many tools, which will guide you through the steps of achieving compliance with the requirements, which will not put the focus on the risks in the beginning. They are a crucial part of the journey, you will get to work with them. Actively decide when and how and search for the right tool to make your work as efficiently as possible.
Structuring your work and sharing responsibilities
After the basic evaluation of your current security posture when evaluating the general themes requirements of a framework, you can start sharing the responsibilities with your team. Who is responsible for which topic? Who has access to the information needed for both, actually filling in the information needed for the requirement and who is able to continuously monitor those as well? It is always a benefit if you have a whole team and not just a single responsible person available. For example, an HR staff member might know better what kind of guidelines are spread in the onboarding, while someone from the IT department knows more about the implementation of a malware protection software. Once the work is spread, each person can continue working with their own responsibilities.
Risk assessment
If you decide to move forward with the conduction of a risk assessment, you will focus on identifying potential threats and vulnerabilities, assessing the potential impact and likelihood of these risks, and determining the appropriate controls to mitigate them.
The risk assessment should be comprehensive, covering all areas of the organization and all types of information assets. Once the risk assessment is complete, the organization should develop a risk treatment plan. This plan outlines the specific actions that will be taken to manage each identified risk. It's important to prioritize risks based on their potential impact and likelihood, and to allocate resources accordingly.
2. Establish a strong information security policy
Another key step is to develop and implement an information security policy. This is an official document accepted by organization's top management, that also clearly defines the organization's information security objectives and the main measures that will be taken to achieve them.
When top management commits to supporting the work and commits to the objectives reached, the propability of reaching those goals increases significantly. In the information security policy the top management usually communicates e.g. their commitment to resourcing, continuously improving the ISMS and thus ultimately reaching the set objectives.
Information security policy should also outline the roles and responsibilities of other staff members in relation to information security.
3. Define your ISMS team
Building a successful ISMS team requires careful selection of individuals with diverse skills and expertise. The team should ideally be composed of members from various departments, including IT, human resources, legal, and operations, to ensure a holistic approach to information security.
The ISMS team should be led by a main responsible person, such as a Chief Information Security Officer (CISO) or an equivalent role. The CISO is responsible for overseeing the overall strategy of the ISMS, ensuring compliance with for example ISO 27001 standards, and communicating with top management about the system's performance.
An ISMS Manager or Coordinator is another important role. This individual is tasked with the day-to-day management of the ISMS, coordinating with different departments, and ensuring the implementation of the ISMS policies and procedures.
IT staff play a vital role in the ISMS team, as they are responsible for implementing and maintaining the technical controls necessary for information security. They should have a deep understanding of the organization's IT infrastructure and the potential security risks associated with it.
Especially for bigger organizations, human resources and even legal professionals are also important members of the ISMS team. HR can help with the training and awareness programs, while legal experts can ensure that the organization's information security policies comply with relevant laws and regulations.
Finally, representatives from other departments can provide valuable input on how the ISMS impacts their operations, and help to ensure that the system is effectively integrated into the organization's overall processes. By clearly defining these roles and responsibilities, an organization can build a strong ISMS team that is capable of achieving for example the ISO 27001 certification.
4. Commit top management
The role of leadership in overcoming ISMS implementation challenges is vital. Leaders are the driving force behind the successful implementation of an ISMS. They set the tone for the organization's approach to information security, establishing the importance of security and the organization's commitment to it.
Leadership is responsible for setting the strategic direction of the ISMS. They define the scope, objectives, and policies of the ISMS, ensuring alignment with the organization's business strategy. This strategic direction provides a clear path for the ISMS implementation and helps to overcome challenges related to scope and direction.
Furthermore, leadership plays a crucial role in resource allocation for ISMS implementation. They ensure that adequate resources, including personnel, technology, and budget, are allocated for the implementation and maintenance of the ISMS. This helps to overcome challenges related to resource constraints.
Lastly, leadership plays a crucial role in continuous improvement of the ISMS. They review the effectiveness of the ISMS regularly, driving improvements and modifications as necessary. This helps to ensure the ISMS remains effective and relevant, overcoming challenges related to changing business and security environments.
5. Ensure employee awareness
Training and awareness programs are also essential for successful ISMS implementation. All staff members should be trained on the importance of information security and their role in maintaining it. Regular training sessions and sharing guidelines for better security awareness can help to create a culture of security within the organization.

Four main ISMS Implementation Challenges
While the benefits of an ISMS are numerous, the path to its successful implementation is not always smooth. From understanding the complex frameworks of standards such as the ISO 27001 to ensuring stakeholder buy-in, organizations often fight with a variety of challenges.
Despite the potential challenges, overcoming these obstacles is not only possible but also a rewarding experience that can significantly enhance your organization's security. In the following sections, we will delve into these challenges and provide practical solutions to help you successfully implement an ISMS in your organization.
1. Dealing with employee resistance
Dealing with employee resistance during the ISMS implementation process is a common challenge. This resistance often stems from a lack of understanding about the system, fear of change, or concerns about increased workload. Therefore, it's crucial to address these issues head-on to ensure a smooth transition. In the end, over 50% of organizations report that implementing ISMS improved their cyber security posture, so your efforts will pay off.
Firstly, it's important to educate employees about the benefits of ISMS and how it can improve the overall security posture of the organization. This can be done through workshops, guidelines, or informative meetings. The goal is to help employees understand the value of ISMS, how it works, and how it will impact their daily tasks.
Secondly, it's essential to involve employees in the implementation process. This can be achieved by creating cross-functional teams that include representatives from different departments. By involving employees in the decision-making process, you can help them feel more invested in the outcome and reduce resistance.
Another effective strategy is to address concerns about increased workload. This can be done by demonstrating how ISMS can actually streamline processes and make tasks more efficient. For example, by automating certain processes, employees can focus on more strategic tasks. Especially ISMS tools may make the efforts very efficient for the employees and may even reduce their workload.
Remember, overcoming employee resistance is not a one-time effort but a continuous process. It requires patience, open communication, and a commitment to fostering a culture of security within the organization. By taking these steps, you can help ensure a successful ISMS implementation.
2. Managing limited resources
Managing limited resources during the implementation of an ISMS is a critical task that requires strategic planning and efficient resource allocation. It involves a careful balance between the available resources and the requirements of the ISMS implementation process.
First of all, it is important to understand that resources are not just financial, but also include time, personnel, and technological resources. A successful ISMS implementation requires a dedicated team with a clear understanding of the organization's information security objectives. This team should consist of members from various departments to ensure a comprehensive approach.
Time
The implementation of an ISMS is not an overnight process. It requires a significant amount of time to ensure that all elements of the ISMS are correctly put in place. Therefore, it's essential to develop a realistic timeline that allows for the careful execution of each step in the implementation process.
Financial resources
Implementing an ISMS can be costly, especially for smaller organizations. It's important to create a detailed budget that covers all aspects of the implementation process, from the initial assessment to the ongoing maintenance of the ISMS.
Technological resources
The right technology can streamline the ISMS implementation process, making it more efficient and effective. This includes software for risk assessment, policy management, and incident management, among others.
Overcoming resource challenges
There are strategies that can help manage limited resources during ISMS implementation. Leveraging existing resources, such as current technologies or personnel with relevant skills, can help reduce costs. Additionally, prioritizing tasks based on their impact on the organization's information security can help ensure that the most critical aspects of the ISMS are addressed first. There are for example some tools, which automatically display you the critical tasks first, so you can start with the highest priority level tasks and parts of your ISMS and continue step by step with the less critical aspects over time (see example picture below: "Priority: critical").

Finally, continuous monitoring and evaluation of the ISMS implementation process can help identify any inefficiencies or areas for improvement. This can enable the organization to make necessary adjustments and optimize the use of resources.
3. Keeping up with evolving threats
Keeping up with evolving threats is a crucial aspect of implementing an ISMS. In the dynamic world of information security, threats are constantly changing and evolving, making it essential for organizations to stay ahead of the curve. This involves continuously monitoring the threat landscape, identifying new vulnerabilities, and updating security measures accordingly.
4. Keeping the ISMS up-to-date
A regular review of the ISMS is an essential component of maintaining and improving the effectiveness of an organization's security posture. It involves a systematic evaluation of the ISMS to ensure it continues to meet the organization's information security needs and objectives. This review is typically conducted on a periodic basis, often annually, but can also be triggered by significant changes in the business environment or security landscape.
During an ISMS review, various aspects of the system are examined. This includes the scope of the ISMS, risk assessment and treatment methodologies, policies and procedures, and the effectiveness of controls. The review also assesses the organization's compliance with relevant laws, regulations, and standards, such as ISO 27001. The goal is to identify any areas where the ISMS may be underperforming or where improvements can be made.
An ISMS review is not a one-off activity, but part of a continuous process of improvement. It should be integrated into the organization's overall governance and management processes. This will ensure that the ISMS remains effective and continues to provide the desired level of information security, thereby supporting the organization's strategic objectives and enabling it to achieve ISO 27001 certification. Some tool let you set automatic review cycles, so you will not loose the overview of them.

Using continuous monitoring third-party audits to ensure ISMS success
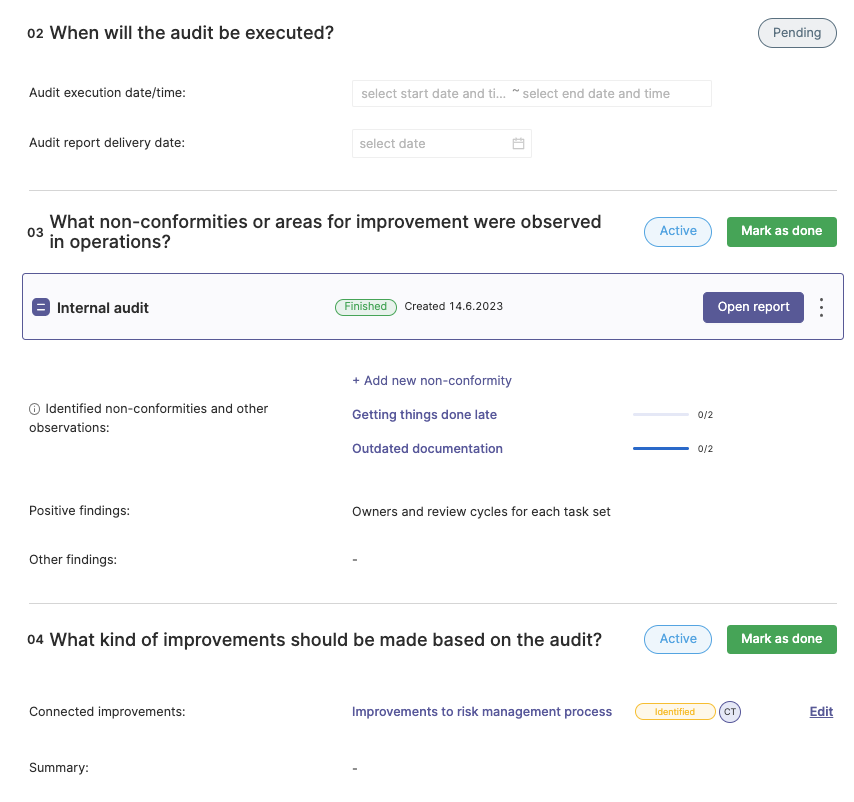
Once the ISMS is in place, it's important to monitor and review its performance regularly. This involves conducting regular audits and reviews to ensure that the ISMS is functioning as intended and that all controls are effective. Any identified issues should be addressed promptly to ensure continuous improvement.
Also for internal audits an organization may benefit from using a tool rather than doing everything by themselves from scratch. An audit tool for example can provide a centralized platform for managing all audit-related activities. This includes scheduling audits, assigning tasks, tracking progress, and documenting findings. It can also facilitate communication and collaboration among the audit team, which can lead to more effective audits.
Further, an audit tool can contribute to continuous improvement. It can provide insights into the effectiveness of the ISMS, identify areas for improvement, and track the implementation of corrective actions. This can help organizations to continually improve their ISMS, thereby enhancing their information security.
You can find some more details about an internal audit feature in action in the Cyberday help article about internal audits.
Conclusion
Overall, a successful ISMS implementation requires careful planning, strong leadership, and a commitment to continuous improvement. By following these steps, organizations can effectively manage their information security risks and achieve for example ISO 27001 certification.
Achieving for example the ISO 27001 certification through a well-implemented ISMS can enhance an organization's reputation, instilling confidence in stakeholders, customers, and partners about its commitment to information security. It can also provide a competitive edge in the market, demonstrating the organization's adherence to best practices in information security management.
Therefore, the effort put into overcoming ISMS implementation challenges can lead to improved business efficiency. By identifying and eliminating redundant processes, organizations can streamline their operations, saving time and resources. In the long run, the benefits of implementing an ISMS far outweigh the challenges, making it a worthwhile investment for any organization concerned about information security.

















